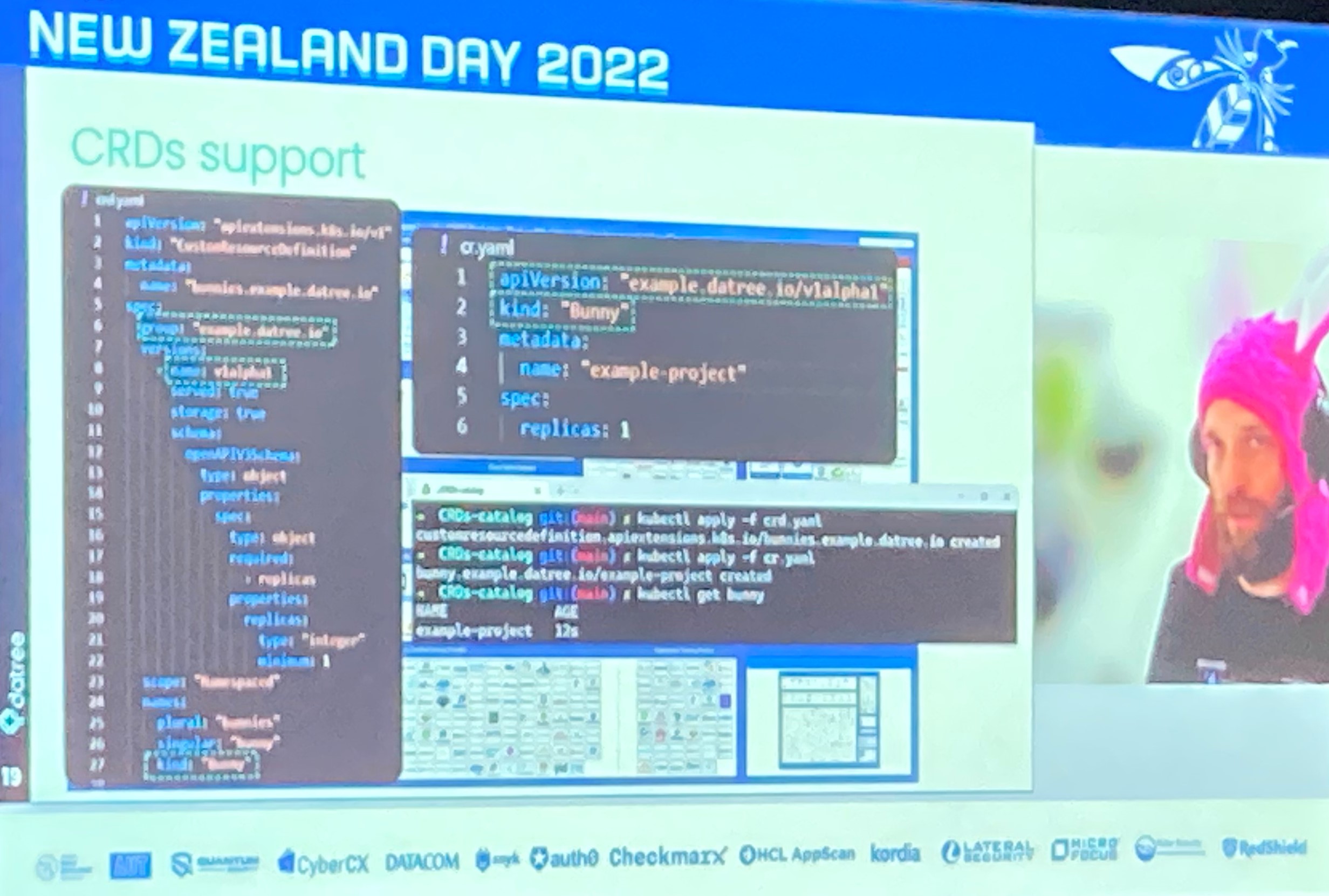
Described as like unit tests for schema, Kubernetes schema validation can ensure your organization’s policies and best practices are applied consistently. This is the first in a series of posts following the OWASP Day 2022.
First tip is that you can get a bunch of value using kubectl --dry-run, but beware of its modes, client or server. Evidently client-mode has been buggy before v1.25, so probably best to stick with the server mode. Of course, kubectl apply will also validate your schema.
For more detailed pre-apply analysis there are a couple of open-source tools recommended. First is Kubeval which was first committed 5 years ago. While it is considered good it isn’t being maintained currently and hasn’t had a commit in over a year.
Better is Kubeconfirm. It is inspired by Kubeval and more actively maintained. It can be incorporated in CI/CD tooling, which is the crux of DevSecOps: to automate scanning for vulnerabilities, and to shift vulnerability discovery earlier in the software development lifecycle.
The remote presenter is Eyar Zilberman from Datree in Israel. He wrote a dev.to post about Kubernetes schema validation here. You can also find more information on the topic from his repositories at github.
To conclude, Kubernetes schema validation is achievable using open-source tools and can be integrated in to your CI/CD pipelines. More complex application of policies and best practice for your organization will require more than basic schema compliance, for that you can check out datree’s solution here.
Check back soon for more posts with information learned from the OWASP Day 2022.